
Cloud Platform
Simple, turn-key cloud planning
The modern data center has become the home of next-generation technologies. The creation of cloud computing and the data-on-demand generation has created new types of challenges for today’s IT environment. Not only do administrators devour to focus on creating robust, multi-tenant, cloud platforms – they must always take end-user performance, resource utilization, and security into consideration. The challenge always becomes deploying an intelligent security model without hindering user productivity.
Our Cloud Platform is a cloud planning platform that enables you to quickly and efficiently build a future-proofed cloud. It is a turn-key solution based on an open and flexible architecture that is designed to run every application workload at scale and with simplicity.

Deploying security at various points
You run a very distributed organization. This means your security solution must be able to scale as well. In some cases, this means deploying virtual security services to various points in your network or cloud environment. The goal is to provide continuous security – and in some cases compliance – to a very large IT infrastructure. Orchestration helps by distributing policies and security protocols to large data centers as well as branch office locations.
Integrating business structure into cloud security
The technology environment has become so critical that many organizations are actually creating their business plan around the capabilities of IT. In many cases, IT administrators are directly integrating their business flow into the structure of their security. This type of orchestration – from business to technology – allows organizations to ensure faster delivery services and improved end-user performance.
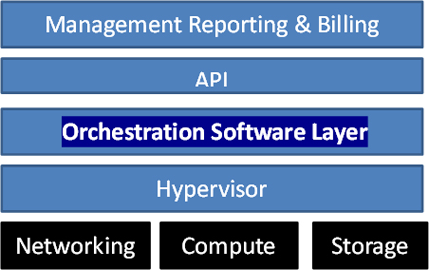
Create data center-to-cloud security policies
Imagine being able to create a visual representation of your security flow. Imagine being able to automatically generate an interactive map of all network firewalls and routers, subnets and zones, and deliver instant visibility of the impact of security policies on network traffic. Now, imagine being able to do this at all of your data center and cloud points. This is the power of security management, orchestration, and edge control. Your environment is connected through a series of routers, gateways, firewalls, and virtual services.